The contemporary enterprise landscape is undergoing a profound and irreversible transformation, a phenomenon driven by the widespread adoption of remote and hybrid work models. This shift, which was dramatically accelerated by the global COVID-19 pandemic, has fundamentally altered the definition of the corporate network perimeter. No longer confined to the physical boundaries of an office, the enterprise is now a distributed ecosystem where the mobile device—be it a smartphone, tablet, or laptop—has become the primary endpoint for business operations. This decentralization presents both an unprecedented opportunity for operational flexibility and a complex array of security and management challenges. In response to this paradigm shift, the market for enterprise mobility management (EMM) solutions has entered a phase of explosive growth. Current projections estimate the global EMM market size at a substantial $33.27 billion in 2024, with a dramatic forecast to grow to $189.02 billion by 2032, exhibiting a remarkable compound annual growth rate (CAGR) of 24.5% during this period. This rapid expansion is not merely a reflection of a technological trend but is a direct, market-wide response to the urgent need for businesses to remotely manage, secure, and monitor their endpoints in a new, borderless reality. The United States, in particular, stands as a dominant force within this market, with a projected revenue of $17,942.6 million by 2030, commanding a significant market share and driving innovation within the sector. This data underscores that adopting a robust EMM solution is no longer a matter of convenience but a strategic imperative for any organization seeking to maintain productivity and fortify its security posture in the modern era.
The Evolution of Endpoint Management: From MDM to UEM
To fully understand the capabilities required of a modern management solution, it is essential to trace the evolution of the technology itself. The journey from a basic mobile device management tool to a comprehensive unified endpoint management platform reflects a growing sophistication in addressing enterprise needs.
Mobile Device Management (MDM): The foundational stage, MDM, focuses on the administration of mobile devices like smartphones and tablets. This device-centric approach is concerned primarily with provisioning and securing the device itself, providing functionalities such as remote tracking, troubleshooting, and wiping of data in case of theft or loss. While effective for a time, this approach became insufficient as the number and variety of endpoints began to proliferate.
Enterprise Mobility Management (EMM): EMM emerged as a natural evolution, building upon the principles of MDM by incorporating mobile application management (MAM). This new focus shifted from just the device to the applications and data residing on it. EMM solutions began to offer more granular control, allowing IT administrators to manage and secure corporate data on employee-owned devices, a critical step for the rise of Bring-Your-Own-Device (BYOD) policies. EMM also introduced solutions for mobile content management and mobile expense management, creating a more comprehensive solution for securing a mobile workforce.
Unified Endpoint Management (UEM): The current standard, UEM, represents the culmination of this evolution. It integrates the management of all endpoints, including not just mobile devices but also laptops, desktops, wearables, and Internet of Things (IoT) devices, into a single, cohesive console. UEM platforms incorporate EMM principles but take them to a new level by providing advanced security features like threat detection, patch management, and automated compliance. The central distinction is one of scale and scope: while EMM focuses on a subset of devices, UEM provides an all-encompassing approach that secures and manages every user, device, application, and policy from one centralized platform, eliminating the need for a fragmented collection of disparate tools.
The Core Business Challenges Driving Adoption
The market growth is fueled by tangible, daily pain points faced by IT leaders. The decision to invest in a unified endpoint management solution is a direct response to a range of pressing security, compliance, and productivity challenges. The most critical of these challenges include:
Compliance Requirements: For industries with stringent regulatory frameworks, such as healthcare (HIPAA) or finance (PCI), secure data handling is not optional. Ensuring that sensitive data is protected on every single device that accesses it is a major driver of MDM adoption, as non-compliance can lead to severe penalties and a loss of public trust.
BYOD Security Concerns: The proliferation of personal devices in the workplace is a double-edged sword. While it can enhance productivity by allowing employees to use devices they are familiar with, it also creates significant vulnerabilities. The IT department loses control over the hardware, making it an uphill battle to dictate what applications are installed, how devices are secured, and when security patches are applied. This loss of control creates an easy entry point for cybercriminals.
Productivity Management: Without a centralized solution, IT teams are left to manage mobile devices and their applications manually, leading to significant time consumption and resource drain. A unified platform is essential for automating tasks like software deployment, security patch updates, and troubleshooting, allowing IT personnel to focus on more strategic initiatives.
The severity of these issues is evidenced by recent statistics. An overwhelming 85% of organizations have faced a mobile cyberattack in the past year alone, with 90% of successful corporate breaches being attributed to mobile phishing attacks. The threats are not theoretical; they are a daily reality. This includes malware and spyware, which can be hidden in seemingly legitimate applications, and data leakage that can occur when employees leave the company, taking confidential files with them on their personal devices. The increasing prevalence of insecure data transmission over unencrypted channels also exposes businesses to "man-in-the-middle" attacks, further solidifying the need for a comprehensive solution.
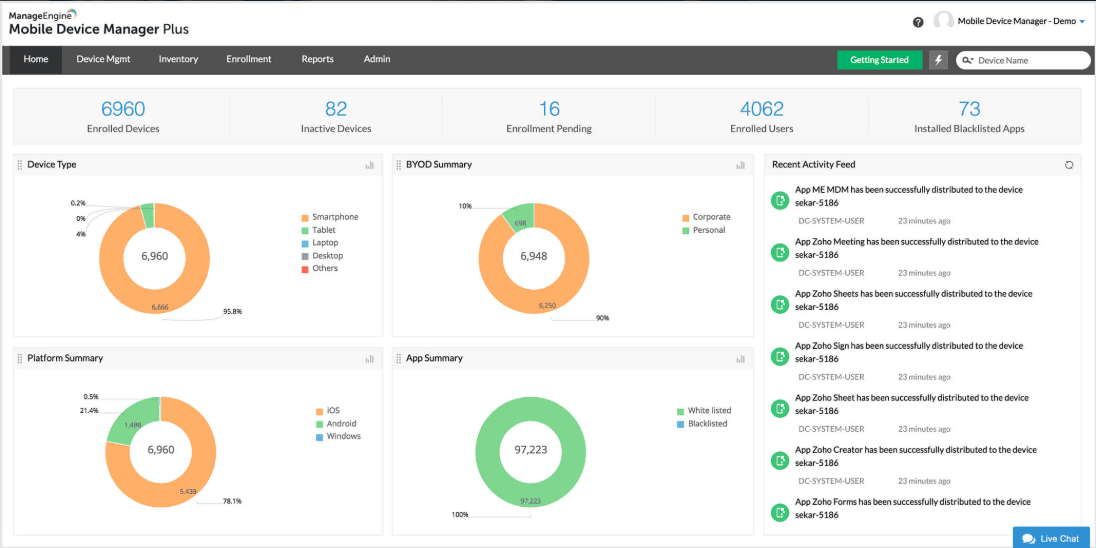
Zoho ManageEngine Mobile Device Manager Plus emerges as a powerful and cohesive response to the complexity and fragmentation of modern IT management. The platform is not merely a collection of standalone features; it is an integrated solution that adheres to a "single pane of glass" philosophy. This approach is designed to centralize and simplify the administration of an entire IT infrastructure from a unified console, including security, networks, servers, and, critically, mobile devices and their applications. This is a direct answer to the problem of IT teams being overwhelmed by the need to manage a multitude of disparate vendor tools, each with its own interface, licensing model, and support system. The platform's integrated nature translates directly to increased operational efficiency and a substantial reduction in administrative overhead. This unified approach is a cornerstone of Zoho's broader ecosystem, which comprises over 130 applications. The ability to leverage one-click integrations between these products, such as connecting Mobile Device Manager Plus with the IT service management platform ServiceDesk Plus, the analytics platform Analytics Plus, or the security information and event management tool Log360, provides a holistic solution for a business's IT needs. This synergy means that a company is not just acquiring a point solution for a single problem but is investing in a cohesive, interconnected, and future-proof IT infrastructure. The unified nature of the platform offers a significant competitive advantage, enabling seamless workflows and providing a comprehensive view of the entire IT landscape from a single vantage point.
A Comprehensive Suite of Features: From Enrollment to Retirement
The robust feature set of Zoho ManageEngine Mobile Device Manager Plus is designed to cover the entire lifecycle of a mobile device, from its initial provisioning to its eventual retirement. The platform offers a wide array of functionalities that provide granular control and automation, ensuring devices are secure and productive from day one.
Automated Enrollment and Provisioning: The solution simplifies the device onboarding process with a variety of automated and manual enrollment options. For corporate-owned devices, it supports advanced methods like zero-touch enrollment for Android devices and integration with Apple Business Manager for iOS, allowing for over-the-air provisioning with minimal user or administrator intervention. For employee-owned devices, it offers self-enrollment or invite-based options, allowing organizations to maintain control while respecting user privacy. Once enrolled, devices can be automatically assigned to groups based on their operating system or type, ensuring they are provisioned with the necessary profiles, configurations, and applications without manual effort. The platform is compliant with a wide range of management models, including Corporate-Owned, Personally Enabled (COPE); Corporate-Owned, Business Only (COBO); and Corporate-Owned, Single Use (COSU).
Comprehensive Application Management: The platform provides a centralized app distribution console, allowing IT administrators to build a custom enterprise app catalog for approved applications. This empowers administrators to silently install, update, and even terminate corporate apps without disrupting the end-user. The ability to distribute apps by department or group ensures that the right users receive the right tools. Furthermore, the platform includes powerful app blocklisting features that automatically remove unapproved public apps and prevent their reinstallation, a critical defense against malware and compliance violations. The platform also offers remote control and troubleshooting capabilities for over 20 vendors, enabling IT to resolve device-specific issues and reduce downtime.
Advanced Security and Compliance: Security is woven into the fabric of the platform. It allows for the enforcement of comprehensive security policies, including device restrictions on hardware buttons, networks, and applications. Administrators can enforce encryption, strong passcodes, and biometric policies to fortify device security against unauthorized access. The platform also provides the ability to detect and report on critical events in real time, such as compliance violations, blocked applications, or the presence of jailbroken or rooted devices. For lost or stolen devices, the solution offers a range of remote commands, including geotracking, remote device lock, and a complete data wipe.
Asset Management and Reporting: Beyond day-to-day management, the platform provides robust asset tracking and reporting capabilities. It can generate detailed reports on all mobile assets and their app inventories. Administrators can also leverage customizable reports to gain deep insights into network health and security posture, ensuring they stay ahead of potential issues.
Reimagining Mobile Security with Zero Trust Architecture
Modern cybersecurity has evolved beyond traditional perimeter defenses, which relied on the flawed assumption that everything inside the corporate network is inherently trustworthy. The rise of cloud services and remote work has made this model obsolete. A more strategic and robust approach is the Zero Trust Architecture (ZTA), a security framework based on the principle of "never trust, always verify". This model eliminates implicit trust and requires continuous authentication and verification for every user, device, and connection before granting access to resources.
Zoho ManageEngine's security features are a natural extension of this ZTA framework. They are not merely a list of protective measures but components of a coherent, strategic security posture.
Continuous Verification and Authentication: The platform facilitates the core tenet of ZTA through features like two-factor authentication (2FA) during device enrollment. This ensures that unauthorized users cannot gain access to corporate resources, even if they have stolen credentials. The system is designed to verify the identity of the user and device at each access attempt, mitigating the risk of a breach.
Least-Privileged Access: The ZTA model mandates that users and devices are granted only the minimum level of access required to perform their assigned functions. Zoho addresses this with
role-based access control, allowing administrators to delegate device management tasks with customizable read and write permissions. This ensures that IT personnel are given only the access they need, minimizing the potential blast radius of a compromised account.
Continuous Monitoring and Risk Adaptation: ZTA requires real-time monitoring to detect and address risks quickly. Zoho provides this capability by generating real-time alerts for compliance violations, inactive devices, or jailbroken devices, enabling IT to respond proactively to potential threats. The ability to track a device's location also ensures it is being used within a specified geolocation, providing another layer of continuous oversight.
This strategic alignment with ZTA demonstrates a nuanced understanding of modern cybersecurity. The platform is built not to prevent all breaches—an impossible task—but to contain and minimize the damage once an attack has occurred. It moves the defense from the porous network perimeter to the individual endpoint itself, providing a far more defensible and resilient security framework.
Advanced Threat Mitigation: Combating Malware, Phishing, and Insecure Networks
The mobile landscape is rife with threats, from sophisticated phishing attacks to hidden malware. Zoho ManageEngine provides a suite of advanced features specifically designed to combat these pervasive challenges.
Defense Against Malicious Applications: A common vector for malware is seemingly legitimate applications downloaded from unofficial sources or even from app stores. Zoho's
App Blocklisting feature is a direct defense against this threat. It allows administrators to predefine a list of unapproved apps that are automatically removed from corporate devices and prevented from being reinstalled, ensuring that only enterprise-approved applications are in use. For devices locked down for a single purpose, such as a point-of-sale system, the
Kiosk Mode feature can lock down devices to an approved set of apps while restricting access to all other device functions.
Protection Against Insecure Networks: Man-in-the-middle (MITM) attacks and network spoofing, where hackers intercept data over unencrypted channels or fake Wi-Fi networks, are significant risks for mobile devices. The platform mitigates this by enabling the configuration of
Always On VPN and the bulk distribution of network settings. This ensures that all data in transit is encrypted and transmitted securely, regardless of the network the device is connected to.
Real-Time Threat Detection: Beyond prevention, the platform provides proactive detection capabilities. It can check a device's integrity and monitor for compliance violations, immediately alerting IT administrators to high-risk or noncompliant devices. This provides the real-time visibility needed to neutralize security threats before they can escalate.
Ensuring Data Integrity and Privacy: The Power of Containerization
The adoption of BYOD policies often faces resistance from employees who fear that IT administrators will be able to monitor their personal data. This "Big Brother" concern can be a major source of friction in an organization. Zoho ManageEngine directly addresses this by providing a clear separation between corporate control and employee privacy.
The platform utilizes containerization to create a secure, encrypted container for all corporate data on a personal device. This sandbox effectively separates work-related data and applications from an employee's personal files, such as photos, messages, and social media apps. This approach protects sensitive information without infringing on user privacy. This feature is particularly valuable in addressing data leakage risks. In the event of an employee leaving the company, the IT department can perform a
"corporate wipe," which selectively removes only the business data from the device while leaving all personal files intact. This capability ensures that valuable company data does not fall into the wrong hands while simultaneously respecting the privacy and ownership of the employee's personal property. This powerful combination of security and privacy makes the solution easier to implement and gain acceptance from the workforce, mitigating a significant source of internal resistance.
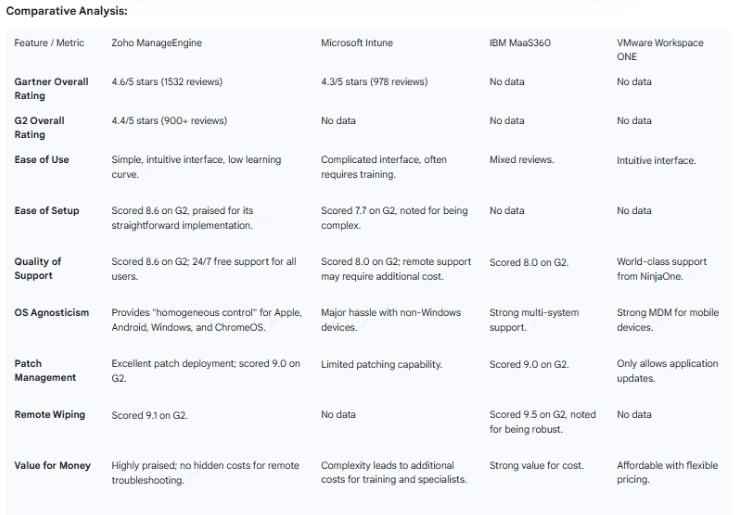
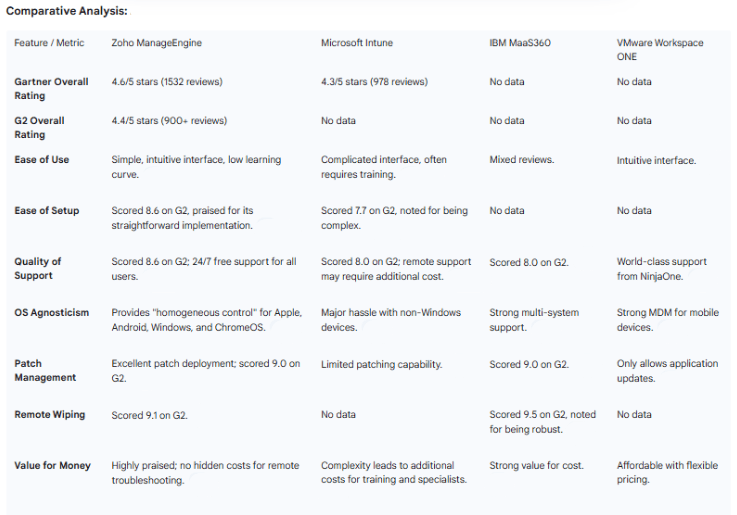
For a professional audience, third-party validation is a crucial indicator of a product's credibility and reliability. Zoho ManageEngine has consistently received recognition from some of the most respected analyst firms and review platforms in the industry, underscoring its maturity and sustained product quality.
Gartner: ManageEngine has been recognized as a "Notable Vendor" in the 2021 and 2023 Gartner Market Guide for UEM tools. The company was also recognized in the Gartner Magic Quadrant for Unified Endpoint Management tools for the fourth time in 2022. The consistency of this recognition from a leading analyst firm over a period of many years is a powerful signal of the platform's reliability and its consistent performance within the market.
Forrester: The platform has been recognized as a "Strong Performer" in The Forrester Wave for Unified Endpoint Management in 2021 and 2023. This standing reflects a strong and growing practice that provides breadth and depth of capabilities to enterprise clients.
G2: On the G2 review platform, Zoho ManageEngine Mobile Device Manager Plus was ranked in the top 50 on the "Best IT Management Products for 2024" list and was awarded the #1 spot for Ease of Admin, Ease of Setup, and Android Support. The platform has consistently received high ratings from a large number of users, with one version of the product receiving an overall score of 4.6 out of 5 stars from over 1,400 ratings on Gartner Peer Insights.
Other Recognition: The solution has also been named the "Best for Large Device Portfolios" by PCMag and has been featured in TechRadar's "Best MDM solutions" lists for multiple years.
The consistent stream of positive reviews, high ratings, and industry accolades from diverse and respected sources demonstrates that the platform is a mature, trustworthy, and proven solution. This validation provides a strong counterpoint to any lingering doubts and positions Zoho as a reliable and defensible choice for any organization.
In an era defined by a decentralized workforce and an ever-expanding threat landscape, the mobile device is a crucial asset and a significant vulnerability. The decision to invest in a mobile management solution is no longer a matter of technical convenience but a strategic investment in the security, productivity, and future growth of an organization. Zoho ManageEngine Mobile Device Manager Plus addresses this strategic imperative with a multi-dimensional approach that. The confluence of these advantages presents a compelling business case for Zoho ManageEngine. It is a strategic tool that empowers businesses to navigate the complexities of modern mobility, protect their valuable data assets, and ensure their employees remain productive and secure, regardless of their location. The platform is not just about managing devices; it is about building a secure, efficient, and scalable foundation for the future of work.

